On March 3, 2020, just before lunchtime in Washington, D.C., Stephen Ryan sent someone at the U.S. Treasury department a thank-you note with a curious
On March 3, 2020, just before lunchtime in Washington, D.C., Stephen Ryan sent someone at the U.S. Treasury department a thank-you note with a curious detail.
The chief operating officer and co-founder of cryptocurrency sleuthing firm CipherTrace, Ryan was one of 16 executives who attended an industry summit the day before with then-Treasury Secretary Steven Mnuchin. Along with his gratitude for the meeting, Ryan attached a slide deck that laid out CipherTrace’s strategy for demystifing crypto wallets. Among those methods: “honey pots.”
This article is part of CoinDesk’s Privacy Week series.
Ryan’s note was part of a 250-page trove of Mnuchin’s emails obtained by CoinDesk through a Freedom of Information Act (FOIA) request. Portions of his slide deck closely resemble CipherTrace’s public promotional materials. Those, too, have referenced “honeypots,” or the rhyming “crypto money pots,” since at least 2018.
What did CipherTrace mean by these terms? The cybersecurity community uses the phrase “honey pot” to describe a decoy target that collects intelligence on unsuspecting attackers. In other words: a trap.
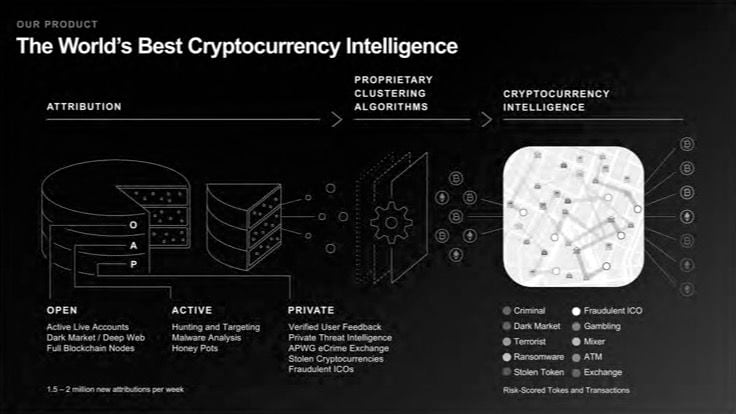
CipherTrace, which payments giant Mastercard purchased last fall for an undisclosed price, is part of a cottage industry that monitors the $14 billion-a-year crossroads of cryptocurrency and crime. Sifting through millions of daily transactions recorded on blockchains, or public ledgers, firms like Chainalysis, TRM Labs and Elliptic search for red flags and illicit movements, labeling suspect addresses as they go.
The companies cast their service as essential to normalizing crypto and stamping out crime. Detractors lambast these tracing firms as on-chain narcs, even though they are primarily working with public information.
CipherTrace wouldn’t be the first company in this niche to set snares in hopes of capturing information that can’t be found on-chain. Chainalysis, the leading crypto tracing vendor, has for years owned a wallet explorer site that captures visitors’ IP addresses and links them to the blockchain addresses they looked up. The company acknowledged this practice only last October, the month after CoinDesk published an article drawing attention to it.
More than half a dozen cryptocurrency industry veterans told CoinDesk they had no idea what CipherTrace meant by “honeypots.” In a statement provided to CoinDesk, the Los Gatos, Calif.-based company gave the basic computer security definition without explaining what it meant in the context of blockchain analysis.
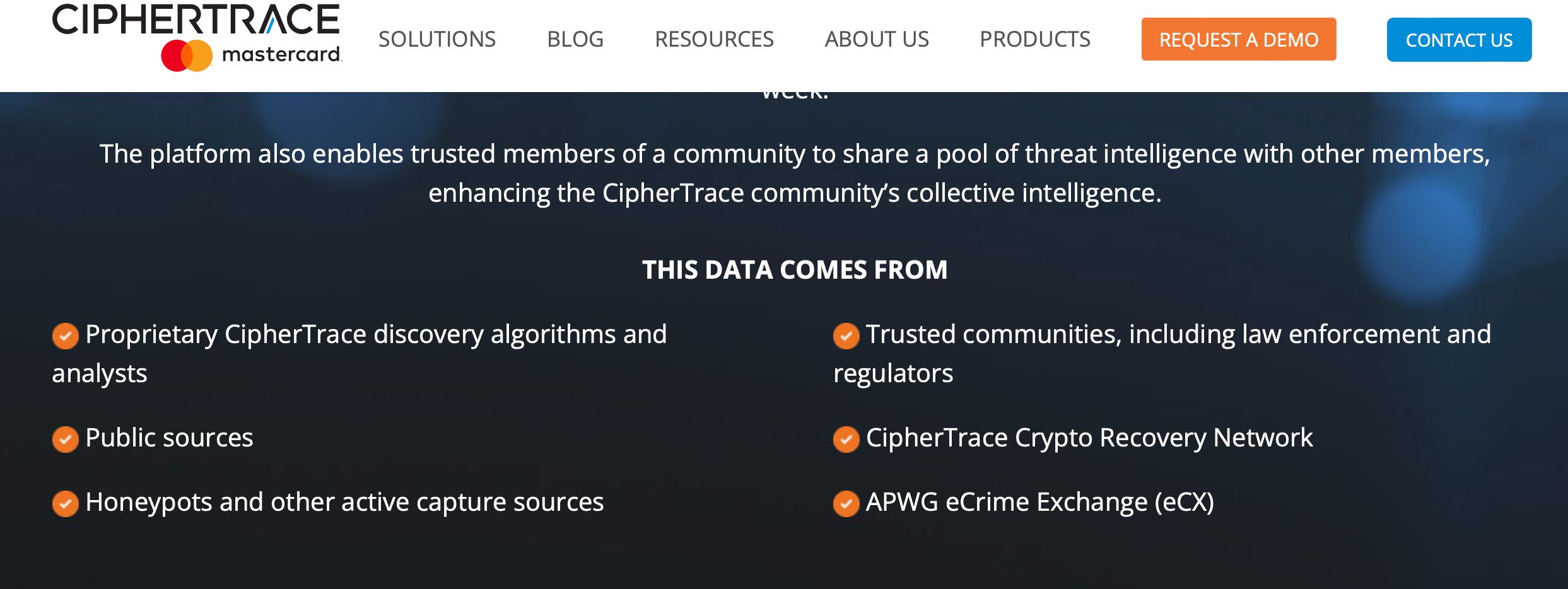
“A ‘crypto money pot’ or ‘honeypot’ is a security term referring to a mechanism that creates a virtual trap to lure would-be-attackers,” CipherTrace said, adding that the documents mentioning these tactics are old. “CipherTrace does not use ‘crypto money pots” anymore, it said (although the company’s website touted both money and honey pots as of Thursday).
CoinDesk asked CipherTrace: “Does your firm collect IP address data for the purposes of linking them to wallet addresses?”
A CipherTrace representative responded: “As a privacy-focused company, CipherTrace does not map IP data to private individuals.”
She did not answer CoinDesk’s question: whether CipherTrace maps IPs to wallets. CoinDesk asked a second time if CipherTrace maps IP addresses to wallet addresses. CipherTrace did not respond.
Such caginess “is a frequent issue in the privacy space, when we talk about network identifiers like IP addresses.,” said Sean O’Brien, a cybersecurity researcher. “Companies try to distance themselves from what you would traditionally call personally identifiable information by saying IP addresses are something else. In fact, they’re incredibly useful for identifying households, businesses and individuals.”
For example, “if you need to investigate a Bitcoin transaction related to a suspected cybercrime, IP addresses are exactly the kind of information you’d be looking for,” O’Brien said. “The earliest cases involving law enforcement and the internet hinge on IP addresses as evidence, for good reason. And, they’re just as useful to harass and stalk people as they are to prosecute them.”
Following the money
Tracing companies have long been a major if underrecognized force in crypto’s institutional march. Fighting back against a tired perception that bitcoin is primarily a criminal finance tool, they parse the data to pinpoint the meager share that actually is.
Chainalysis recently estimated that 0.15% of crypto transactions in 2021 were illicit – by far the smallest percentage on record. (“Illicit” wallets amassed a record-high $14 billion last year, a seemingly paradoxical stat that Chainalysis attributed to crypto’s booming growth.)
CipherTrace says its mission is to “grow the cryptocurrency economy by making it trusted by governments, safe for mass adoption, and protecting financial institutions from crypto laundering risks.”
Taken from the presentation shared…
www.coindesk.com